Generate Trafic
IP traffic going to and from network interfaces in VPC A is now being collected in CloudWatch. Generate some traffic between the VPC A Private AZ1 Server Amazon EC2 instance in VPC A, and the VPC B Private AZ1 Server instance in VPC B using iperf (a widely used tool for network performance measurement and tuning).
After generating the traffic, continue to the next step to view the flow log in CloudWatch.
Review Security Group for EC2 instance in VPC B
A Security Group rule for the Amazon EC2 instance in VPC B has been created for you to allow the iperf server to receive incoming traffic.
-
In the EC2 Dashboard navigate to Instances
-
Select the check box next to the
VPC B Private AZ1 Serverinstance, scroll down and click on the Security tab below and click on the Security groups link forsg-xxxxxxxx (VPC B Security Group)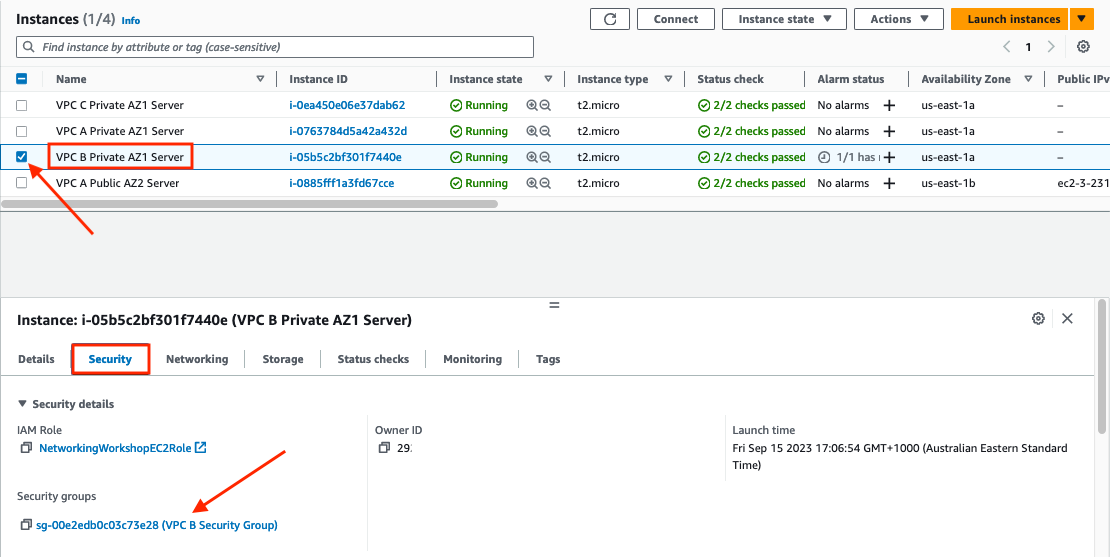
-
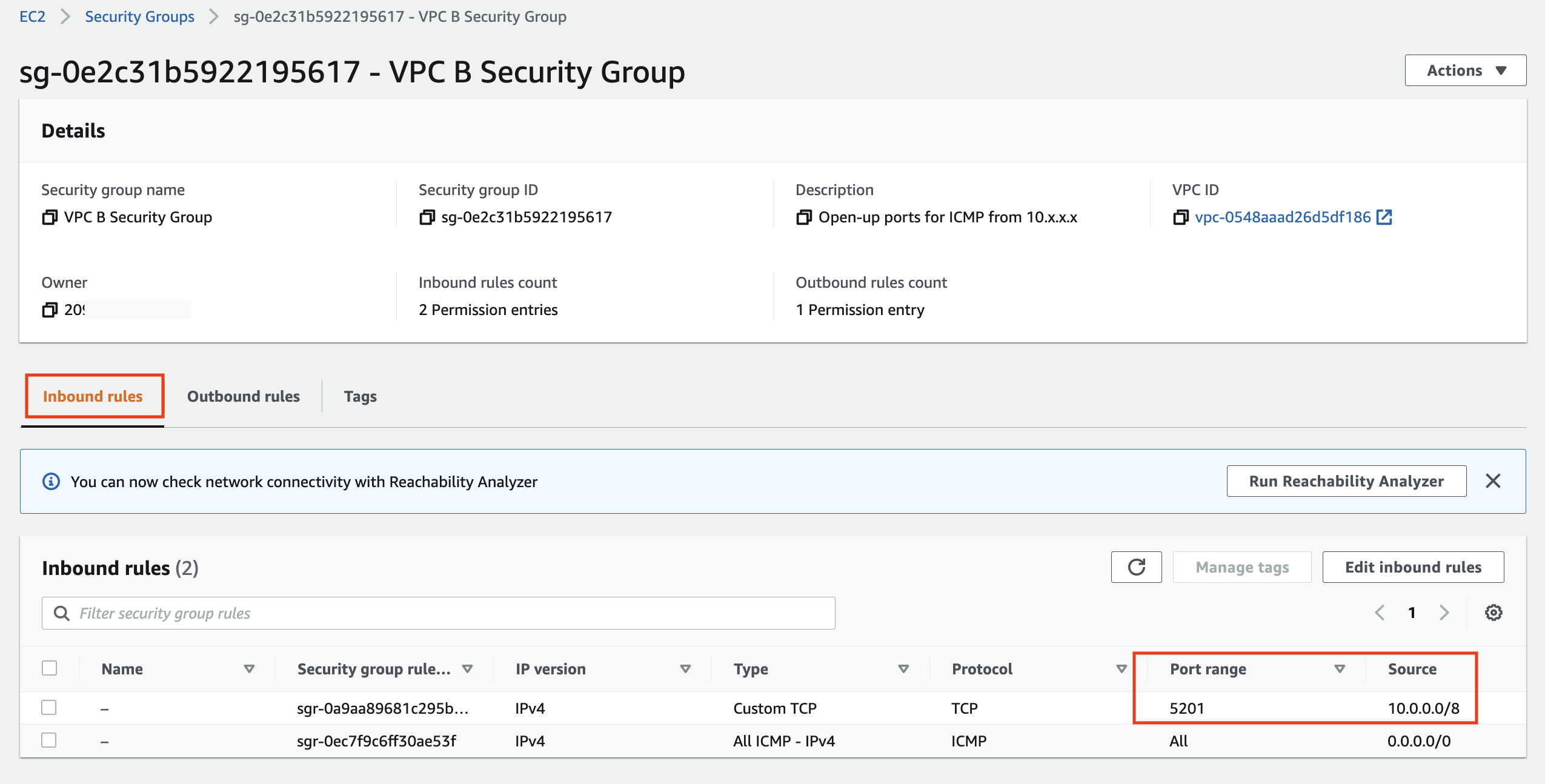
In the Security Group screen that opens scroll down to the Inbound rules tab and confirm that port 5201 is open for TCP traffic from 10.0.0.0/8
Install and run iperf3 server on EC2 instance in VPC B
-
In the EC2 Dashboard navigate to Instances
-
Select the check box next to the
VPC B Private AZ1 Serverinstance, click Connect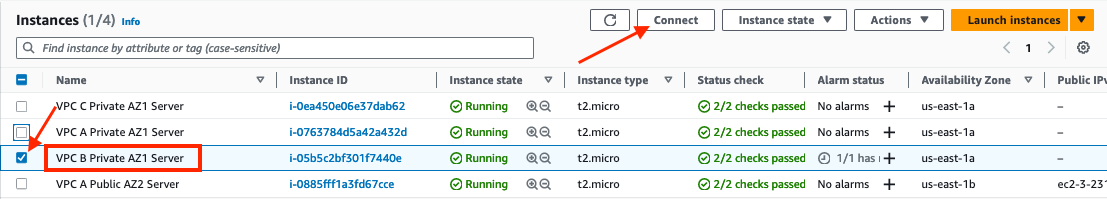
-
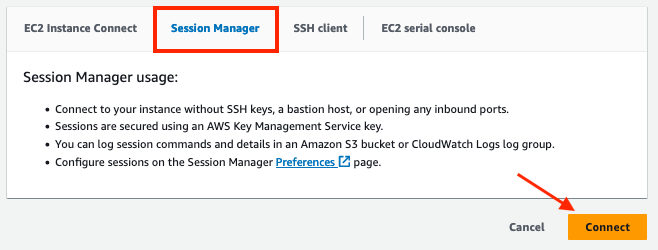
Click Connect again in the Session Manager tab to open a command prompt
-
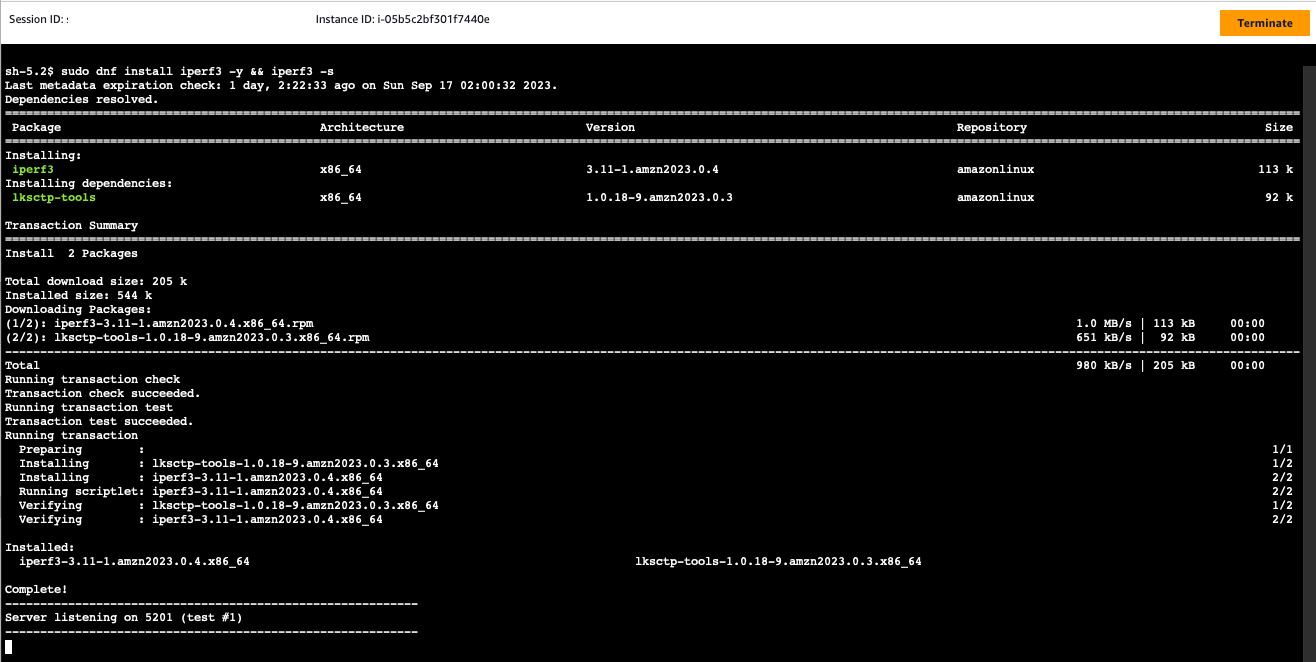
Install and start the iperf server on the EC2 instance in VPC B:
sudo dnf install iperf3 -y && iperf3 -s
-
Leave the Session Manager browser tab open, switch back to the Connect to instance tab and click on the Instances link
-
Select the check box next to the
VPC A Private AZ1 Serverinstance, and click Connect
-
Click Connect again in the Session Manager tab to open a command prompt

-
Install iperf and set up a TCP transfer with 2 parallel streams for 30 seconds to the EC2 instance in VPC B.
sudo dnf install iperf3 -y && iperf3 -c 10.1.1.100 -P 2 -t 30
Connecting to host 10.1.1.100, port 5201
[ 4] local 10.0.1.100 port 37860 connected to 10.1.1.100 port 5201
[ 6] local 10.0.1.100 port 37862 connected to 10.1.1.100 port 5201
[ ID] Interval Transfer Bandwidth Retr Cwnd
[ 4] 0.00-1.00 sec 64.9 MBytes 544 Mbits/sec 18 429 KBytes
[ 6] 0.00-1.00 sec 57.5 MBytes 482 Mbits/sec 16 380 KBytes
[SUM] 0.00-1.00 sec 122 MBytes 1.03 Gbits/sec 34
- - - - - - - - - - - - - - - - - - - - - - - - -
[ 4] 1.00-2.00 sec 59.6 MBytes 500 Mbits/sec 15 322 KBytes
[ 6] 1.00-2.00 sec 59.0 MBytes 495 Mbits/sec 25 256 KBytes
[SUM] 1.00-2.00 sec 119 MBytes 994 Mbits/sec 40
- - - - - - - - - - - - - - - - - - - - - - - - -
[ 4] 2.00-3.00 sec 64.6 MBytes 542 Mbits/sec 20 330 KBytes
[ 6] 2.00-3.00 sec 55.4 MBytes 465 Mbits/sec 23 223 KBytes
[SUM] 2.00-3.00 sec 120 MBytes 1.01 Gbits/sec 43
- - - - - - - - - - - - - - - - - - - - - - - - -
[ 4] 3.00-4.00 sec 49.6 MBytes 416 Mbits/sec 25 280 KBytes
[ 6] 3.00-4.00 sec 69.3 MBytes 581 Mbits/sec 15 272 KBytes
[SUM] 3.00-4.00 sec 119 MBytes 998 Mbits/sec 40
- - - - - - - - - - - - - - - - - - - - - - - - -
...
- - - - - - - - - - - - - - - - - - - - - - - - -
[ 4] 28.00-29.00 sec 59.7 MBytes 501 Mbits/sec 13 396 KBytes
[ 6] 28.00-29.00 sec 54.9 MBytes 460 Mbits/sec 14 330 KBytes
[SUM] 28.00-29.00 sec 115 MBytes 961 Mbits/sec 27
- - - - - - - - - - - - - - - - - - - - - - - - -
[ 4] 29.00-30.00 sec 62.9 MBytes 528 Mbits/sec 11 330 KBytes
[ 6] 29.00-30.00 sec 51.4 MBytes 431 Mbits/sec 17 289 KBytes
[SUM] 29.00-30.00 sec 114 MBytes 959 Mbits/sec 28
- - - - - - - - - - - - - - - - - - - - - - - - -
[ ID] Interval Transfer Bandwidth Retr
[ 4] 0.00-30.00 sec 1.78 GBytes 508 Mbits/sec 412 sender
[ 4] 0.00-30.00 sec 1.77 GBytes 508 Mbits/sec receiver
[ 6] 0.00-30.00 sec 1.66 GBytes 474 Mbits/sec 441 sender
[ 6] 0.00-30.00 sec 1.66 GBytes 474 Mbits/sec receiver
[SUM] 0.00-30.00 sec 3.43 GBytes 983 Mbits/sec 853 sender
[SUM] 0.00-30.00 sec 3.43 GBytes 982 Mbits/sec receiver
iperf Done.
- When iperf completed with an iperf Done. message, terminate the Session Manager connection on the VPC A instance and switch to the Session Manager tab for the connection to the VPC B instance and terminate that session too.
You have successfully generated traffic between the two instances. The next step is to view the flow log in CloudWatch.